Business
10 Crucial Stages of Incident Response Assistance
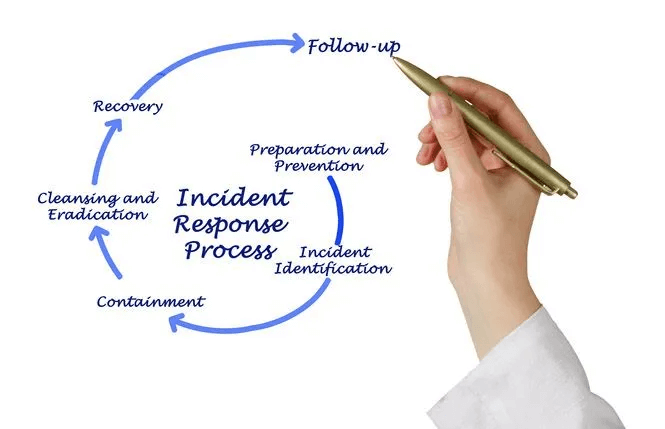
An incident response plan is a documented, written plan with distinct phases that help IT professionals and personnel notice and respond to a data breach or cyber assault.
Creating and managing an incident response strategy requires training and updates. Following a proper process to create an incident report lowers the chances of loss the next time around.
Once followed, there are 10 crucial stages of incident response assistance that can help the IT help desk management team and the rest of the organization understand why certain incidents happened, who was affected, and how the particular environment can be improved. Let’s have a look at these stages:
Table of Contents
1. Define “incident” as per your organization
Before planning for an incident, define your organization’s security incident criteria. First, collect documents to discover how an incident is described in customer contracts, compliance standards, and regulations that may define a security incident for your firm. Next, run through certain scenarios with key stakeholders (security leadership, business unit leadership, legal, compliance, etc.) to decide if they are incidents. Get stakeholder approval on your draft definition. This definition explains when to use an incident response plan.
2. Determine Your Incident Plan’s Scope
Consider whether the incident response plan is for the whole firm or just one specific environment. Your plan can apply to a single system, business unit, or organization. Consider establishing a consolidated incident response strategy that all plans reference.
Most IT service desk management firms opt to use the same procedure regardless of whether a portion of the company is affected, but the stakeholders alter based on the environment.
Also, ensure to cover inadvertent, non-malicious incidents because of their impact on your organization.
3. Train and Identify Stakeholders
Identifying every stakeholder in the incident response process might be time-consuming, but it’s a crucial step in building and maintaining your plan. Best practices recommend having legal, PR, and HR contacts, but there are others too.
Best practices require that incident response contacts, technical contacts, business leadership, and customer impacting groups (legal, PR, customer success) be involved in each environment and documented in a case management system. When an issue affects that environment, you can rapidly pull these groups into incident reports.
Once you’ve identified all your stakeholders, list their roles in incident response. Train your stakeholders on the incident response process so they know what to expect. Set up a program for quarterly or annual refresher training on the incident response procedure and a way for alerting stakeholders on any modifications.
4. Determine Response for Incident Process
There are several incident response models, including:
● Prepare.
● Detect.
● Respond.
● Investigate.
● Contain.
● Eradicate.
● Remediate.
● Lessons Learned.
Determine your process at a high level, then detail each phase.
In “Detect phase,” you may have these steps:
● Determine if the security alert or email constitutes an incident.
● Classify incidents by type, severity, and sensitivity.
● Case management system incident
● Environment impacted
● What’s happening?
● Type events
● Severity ratings
● Determine customer impact
● Appoint Incident Commander
● Incident Commander
● Inform incident commander
Your organization’s process may be different, but it should be documented and understood by stakeholders.
Also, Check – What is Process Excellence?
5. Define Severity level
Severity levels dictate response and organization impact. You don’t want too many severity levels to delay incident classification. Make sure all teams in your organization are at the same level of understanding when talking about the severity level of an incident. This allows them to know the impact of an incident on the organization, whether it’s an IT outage or a security incident.
6. Create An Escalation Matrix And Communications Plan
Incident response requires knowing how to communicate securely, with whom, and when. Before an incident, figure out these logistics because several communication routes can get chaotic.
Things to consider when Communicating during a security incident:
● When communicating security incident details, use the “need to know” approach.
● Create Truth-source.
● Communicate better.
● Set expectations for notifications and updates.
● Consider out-of-band approaches.
Use an Escalation Matrix to track who’s contacted, how, and when. Signing off on the Escalation Matrix sets expectations for initial notification and updates.
For high-severity crises, use an automated notification system to contact parties to join a bridge. Send a concise summary of the incident, its impact, present conditions, response tasks (actions), and any needs the response team has to respond efficiently.
7. Identify Incident Types to Determine Playbooks.
IRPs drive high-level processes, whereas playbooks specify how to respond to specific incidents. Focus on the environment and notice how incidents affect your company? Note that no standard list fits all groups.
Most organizations should have malware, DDoS, illegal access, and other incident types.
Identifying event categories helps you design playbooks. Playbooks for specific incident types should comprise 90% of that type’s incidents. There will always be events where the playbook won’t work; these are usually complex, high-severity incidents.
Here’s an incident playbook example:
● Detection of incidents
● Depending on incident characteristics, the severity level.
● Roles and responsibilities of incident stakeholders
● Case specifics
● Documentation
● Standard Response Tasks with instructions
● The incident is resolved
Playbooks guarantee incident handlers handle events consistently no matter where they’re based. Additionally, it ensures all stakeholders know how organization respond to specific situations.
8. Make an Emergency Plan
Once you’ve done the groundwork, compile it. After developing the strategy, give stakeholders read-only access to the latest version.
9. Plan Ahead
You must implement your plan to train all stakeholders. Testing the plan identifies detection and response gaps. Plan testing can take 60 minutes. Exercise goals:
● Ensure all stakeholders understand the process and role
● Identify detection, response, and containment gaps.
● Identify process flaws
Conduct table-top exercise when your company is:
● New surroundings
● Changing environments
● Shifting roles
*Test your plan at least every quarter.
10. Improve
Continue improving your IRP. No security incident is flawless. Always review occurrences to see where process changes, greater training, or new technology could help detect and respond faster.
Need Help?
At Atlas Systems, they offer the best mediums to assist your organization to grow. They focus on learning and improving, so you can benefit from the best services and efficient results.

-

 Business3 years ago
Business3 years agoHow to Do Long-Distance Moves with Children
-

 Travel2 years ago
Travel2 years agoQuick Guide: Moving To Santa Rosa?
-

 Real Estate3 years ago
Real Estate3 years agoWhy Dubai Festival City is a Great Neighbourhood for Young Learners
-

 Business3 years ago
Business3 years agoIs Guest Posting a Good Inbound Marketing Strategy?
-

 Business1 year ago
Business1 year agoThe Ultimate Guide To Thriving In Your Printing Franchise
-

 Business1 year ago
Business1 year agoExploring The Benefits And Challenges Of Restaurant Franchising
-

 Tech3 years ago
Tech3 years agoCyber Table That Will Change Your Life
-

 Lifestyle1 year ago
Lifestyle1 year agoDallas’ Hidden Gems: 6 Must-Try Restaurants Off The Beaten Path!









Recent Comments